PCI Compliance FAQ
What does PCI stand for?
The term PCI refers to The Payment Card Industry Data Security
Standard - also known as PCI DSS. This is a set of standards to make
sure any company that accepts, processes, stores, or transmits credit
card information is secure.
The PCI DSS is set and managed by the Payment Card Industry Security
Standards Council (the
PCI
SSC
) founded on September 7th 2006. This is an
independent body set up by many of the large credit card brands
including Visa, MasterCard, JCB, Discover, and American Express.
Security standards in the Payment Card Industry (PCI) are always
improving to keep payment account security at its highest all
throughout the transaction process. The PCI council is not held
responsible for making sure members of a transaction follow security
standards, this is always down to the acquirer or payment brand.
Who does the PCI Data Security Standard (PCI DSS) apply to?
All organizations who accept, process, store, or transmit any credit
card information should follow the PCI DSS. The number of
transactions or size of the organization is irrelevant.
Can anyone see the PCI DSS?
Yes, you can find the PCI Data Security Standard on the PCI Security
Standards Council website
here
.
What levels of PCI compliance are there? And which merchant falls
into which?
Based on the number of Visa transactions a merchant has carried out
in the past 12 months, they will fall into one of four levels. The
number of transactions for a merchant Doing Business As (DBA)
includes all prepaid, debit, and credit card transactions. Visa
acquirers have to include the volume of transactions from all DBAs if
an organization has more than one name that it does business as. If
the corporate entity doesn’t aggregate transaction data for more
than one DBA, Visa acquirers will carry on considering only the DBA’s
individual transaction volume to work out what their merchant level
is.
Visa defines the four merchant levels as follows:
Merchants processing over 6 million Visa transactions every year
including all channels
or a merchant classed as a global
level one merchant.
Merchants which process between one and six million Visa
transactions per year over all channels.
Merchants processing over 20,000 and under one million Visa
e-commerce transactions a year.
Only e-commerce merchants which process fewer than 20,000 Visa
transactions per year.
Any merchant that has been compromised may be escalated to a higher
merchant level by Visa.
What does a level 4 merchant need to do in order to comply with
the PCI DSS requirements?
First, you will need to look at the following chart to work out which
Self-Assessment Questionnaire (SAQ) your business must use to comply:
You then need to fill in the
Self-Assessment
Questionnaire
that applies to your business.
If your business comes under the categories of A-EP, B-IP, C,
D-Merchant, or D-Service Provider, you will need to pass a
vulnerability scan with an Approved Scanning Vendor (ASV).
The Attestation of Compliance must be completed by a Qualified
Security Assessor (QSA) or merchant to comply with the PCI DSS. This
can be found in the SAQ tool.
Finally, the business must submit the Self-Assessment Questionnaire
along with evidence of passing a vulnerability scan (if applicable),
and The Attestation of Compliance, and any other documents requested
by your acquirer.
Does the PCI DSS still apply to me even if I only accept card
payments over the phone?
Absolutely. Any business that stores, processes, or transmits
transaction data has to comply.
Does an organization need to be PCI compliant if it uses a
third-party processor?
Still yes. The company will still need to comply with the PCI DSS
even if they use a third-party processor. The only way this helps is
that it may decrease risk exposure and effort to prove compliance.
If a business operates from multiple
locations, do they all need to show PCI DSS compliance?
Usually validation is only required once per year for all locations
if your business locations all come under the same tax ID. You must
also pass and submit a scan carried out by an
Approved
Scanning Vendor (ASV)
if required under the
Self-Assessment Questionnaire.
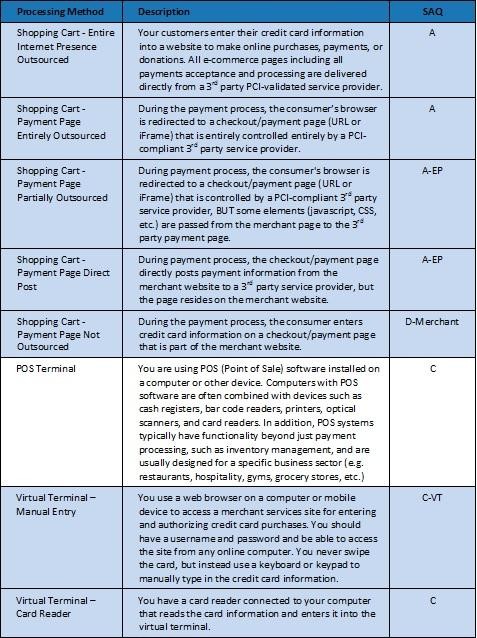
My business only does e-commerce, which Self-Assessment
Questionnaire should I use?
This depends on which setup you use for the shopping cart section of
your site. Take a look at this chart by
ControlScan
to work out which SAQ applies to you:

Does my business still need to comply with the PCI DSS if it
doesn’t store any payment data?
Yes, PCI compliance applies to any organization that accepts credit
or debit cards as a form of payment. It may be easier to comply with
the PCI DSS than it is to store card data, as this always carries
some level of risk.
Which cards are classed as in scope for PCI?
This includes any card that is branded with the five PCI SSC
participating logos - Visa, MasterCard, JCB, Discover, and American
Express. This applies regardless of whether the card is a debit,
credit, or prepaid card.
I have an SSL certificate on my site, does this make me PCI
compliant?
SSL certificates can’t prevent intrusions or malicious attacks,
therefore they do not make a business PCI compliant. An SSL
certificate secures the connection between the web server and the
browser of the customer, and it shows that the owners of the website
are a legitimate organization, but it does not provide PCI
compliance.
What methods can I use if I want my business to store credit card
data?
You may want to store card data if you want to set up recurring
billing. The most secure way to do this is to use a tokenization
service provider and have them look after the data for you. They will
keep it all in a vault and give you a token that can be used for
recurring billing. Doing this removes the risk from your business and
puts it in the hands of someone who has maximum security to keep the
credit card data safe.
Storing this type of data yourself would require high standards of
security, which may need to be checked by a
Qualified
Security Assessor (QSA)
in order to comply with the
PCI DSS.
What if I don’t comply with the PCI DSS?
Failing to comply can result in hefty fines, increased transaction
fees, or even refusal of a bank working with you. Your merchant
account agreement will outline your exposure if you’re unsure.
Making sure you follow PCI not only helps your customers stay safe
from cybercrime, it will also help you to avoid fines of up to
$100,000 per month.
What do the PCI Security Standards Council (PCI SSC) class as
‘cardholder data’?
This means at least the full Primary Account Number (PAN). It can
also include other customer details such as the service code,
expiration date, or cardholder name.
Any security-related information used to authenticate cardholders or
authorize payment card transactions may be transmitted or processed
but may not be stored as part of a payment transaction. This is known
as Sensitive Authentication Data.
What does the PCI SSC define as a ‘merchant’?
Any entity that accepts payment from cards branded by a member of the
PCI SSC (Visa, MasterCard, American Express, Discover, or JCB) in
exchange for goods or services is classed as a merchant. Note that
being a merchant is not mutually exclusive from being a service
provider.
What is the definition of a ‘service provider’?
Any business entity that is not a payment brand and is not directly
involved in processing, storing, or transmitting cardholder data. Any
company providing services that could impact or control the security
of cardholder data is also classed as a service provider.
What does the term ‘payment application’ mean?
In relation to PCI compliance, any piece of software that has been
designed to handle card data is known as a payment application. This
includes anything that transmits, processes, or stores credit card
data electronically. A Point of Sale (PoS) system like those used in
restaurants and bars is classed as a payment application, and so is
any e-commerce shopping cart used on a website.
What is the definition of a ‘payment processor?
Also known as a ‘payment gateway’ or ‘payment service provider
(PSP)’, a payment processor connects a merchant to the bank or
processor that handles the connection to the card brand. The payment
processor handles card transactions on behalf of a merchant or other
entity and routes inputs taken from applications to the appropriate
bank or processor.
What is the Payment Application Data Security Standard (PA-DSS)?
The PA-DSS is maintained by the
PCI
SSC
to ensure the security of payment applications. It
is there to make sure that any vendor provides products in line with
a merchant’s compliance with PCI DSS and avoids storing any
cardholder data. Any application validated by the PCI SSC is
maintained and published in a list.
Can you print the Primary Account Number (PAN) on a customer’s
receipt?
To comply with the PCI DSS, the full credit card number must be
sufficiently masked so that only the first six and last four digits
are displayed at most. Any paper receipt in possession of a merchant
must comply with the PCI DSS in order to ensure security. This does
not supersede other requirements regarding displays of cardholder
data such as the
Fair
and Accurate Credit Transactions Act
(FACTA) or other
laws regarding paper receipts.
Is a vulnerability scan required to be PCI compliant?
The vulnerability scan only applies to certain Self-Assessment
Questionnaires (SAQs), or merchants storing cardholder data after
authorization. If you qualify for this, your business must be scanned
by an Approved Scanning Vendor (ASV) every quarter. The following
SAQs are required to pass an ASV scan:
A-EP
B-IP
C
D-Merchant
D-Service Provider
What’s involved in a vulnerability scan?
An Approved Scanning Vendor (ASV) will carry out the scan using an
automated tool to search for vulnerabilities in a merchant or service
provider’s system. The scan is non-intrusive and requires no
software to be installed, nor any denial of service (DOS) attacks. It
involves reviewing web applications and networks based on the IP
addresses given by the service provider or merchant. The ASV will be
able to identify any vulnerabilities you may have that would allow
hackers to gain access to a private network through an operating
system, service, or device.
Do I have to have a vulnerability scan more than once?
Yes, an Approved Scanning Vendor (ASV) will need to conduct a
vulnerability scan once every 90 days. Your acquirer will determine a
timetable letting you know when to submit successful scan reports in
order to be PCI compliant.
What happens if I don’t comply with the PCI DSS?
As it was created by the major card brands (Visa, MasterCard, Amex,
JCB, and Discover), PCI is not an official law. Any merchant that
doesn’t comply with the PCI DSS may be fined, subject to costs, or
suffer damage to the brand’s reputation if security is compromised.
Complying with the PCI DSS carries some cost and effort upfront, but
hugely decreases the risk of facing these consequences in the long
run.
Am I more vulnerable to hackers if I run my business from home?
Operating from home will often carry with it more vulnerabilities
than a professional environment. This is due to home users often
leaving their internet always on, as well as the personal use of
software like file sharing applications and games which can sometimes
be exploited. If hackers know that a business is run from an owner’s
home, they may be more likely to target it. An Approved Scanning
Vendor can help to scan for vulnerabilities and help home-based
businesses to improve their security.
What should I do if security is breached or my business is the
victim of a cyber attack?
PCI compliance will protect you from most vulnerabilities and
exploits. However, it is not the be all and end all; there is always
a slim chance that hackers could breach your security measures.
It’s important to know what to do if you’re ever targeted. Take a
look at the following resources to help prepare in case of a breach:
Responding
to a Data Breach – A How-to Guide for Incident Management by the
PCI Council
Best
Practices for Victim Response and Reporting of Cyber Incidents by the
Department of Justice
Data
Breach Response: A Nine-Step Guide for Smaller Merchants by
Electronic Transactions Association (ETA)
Are there laws requiring entities to notify affected individuals
of a security breach?
In the U.S., nearly every state now has laws in place requiring
security breach notifications. At the time of writing,
48
states
legally require private, governmental, or
educational entities to notify anyone affected by a security breach
involving personal information. The first state to implement these
laws was California - back in 2003.



